Introduction
Over the years, I’ve had the privilege of speaking with many Security Analysts and Threat Hunters, each with their own approach to threat hunting. Some methods have been truly impressive, and others have been a little less so. While I don’t believe there is necessarily a wrong way to perform threat hunting, there are certainly ways that are more effective. In this post, I will outline some concepts that make for an efficient and impactful threat hunt.
Before we dive into the mechanics of effective threat hunting and work through an example, it’s essential to understand why threat hunting is so important. Framing this will help guide how we approach our hunts. Here are some reasons threat hunting is critical:
Threats are often discovered after a compromise has occurred or a vulnerability is disclosed.
Detections are typically based on past observations, leaving gaps for novel attacks.
Threats can linger undetected for days, weeks, months, or even years before they’re uncovered.
While there are other reasons, these three points lead to one crucial concept: we won’t always detect new threats before they’ve been discovered. Knowing this helps us become more strategic in our approach to finding malicious activity, and in this post, I’ll explain how to hunt with these concepts in mind.
The Pyramid of Pain
If you are unfamiliar with The Pyramid of Pain by David Bianco you are in for an earth shattering revelation in your threat hunting! Okay, maybe not earth shattering, but if your threat hunting is based strictly off searching for hashes, IPs and domains, you may benefit from understanding the concepts behind it.
If you want to read more about it you can read about it here, but the TL;DR: “This simple diagram shows the relationship between the types of indicators you might use to detect an adversary's activities and how much pain it will cause them when you are able to deny those indicators to them.”
When applied to threat hunting, we understand that searching for an IP address or Hash, may not be the best way to find the threat as these things frequently (and easily) change. Instead, focusing your threat hunting on indicators toward the top of the pyramid is far more productive.
Prioritizing The Hunt
Another common mistake I see threat hunters make is looking for a shiny object without really considering whether or not the threat is actually relevant or just something they personally found interesting. If there is some scary sounding Linux exploit out there, but your organization has one Linux server in the basement that isn’t exposed to the internet, it may not be the most important place to hunt.
Consider - Does this threat target my sector or industry? Is there a high probability I may be impacted? Do I have a lot of exposure to this threat?
If the answers to these questions are “no,” it might be worth re-prioritizing your hunt. Of course, if you have the resources to investigate more obscure threats, go for it—but for most, focusing on high-probability, high-impact threats is the most effective use of time and resources.
Continuous Improvement
The last and one of the most important components of threat hunting is ensuring that each hunt has some form of output and a way to measure them. These should be part of a continuous improvement philosophy that drives your hunts. If you are simply hunting for a threat and not building new detections, improving telemetry, or improving your controls - you are doing it wrong.
I recommend tracking the following at a minimum:
Hunt Environment: (Windows, MacOS, Linux, Cloud, etc)
Number of new detections added
Number of telemetry improvements
Threat found (Yes/No)
Also, be sure to document your hunt and what you’ve learned. Your documentation will help describe what is normal for your environment, which can be valuable if you’re ever investigating an incident. Documenting your hunts is also important for both rerunning them in the future and continuously improving them over time.
Putting It Together: A Practical Example
So we have covered why we hunt, what to hunt for, and how to prioritize our hunts. Next let's walk through an example hunt.
First let's pretend we are the threat hunters responsible for protecting a hospital. We receive this advisory related to BlackSuit (Royal) Ransomware who is known to target healthcare. That checks one of our priority boxes!
In this report there are tons of IOCs (indicators of compromise) and TTPs (tactics, techniques and procedures) that are utilized by the ransomware group. Should we search for the hashes, filenames, IPs or domains? That might work. Instead I am going to focus on something at the top of the pyramid of pain.
In the report we see the threat actors use a tool called Chisel.
Chisel is a tool that can be used by attackers for various nefarious purposes. It can be used for C2 (command and control), data exfiltration, bypassing firewalls, etc. A few TTPs that map back to MITRE are:
T1071.001 - Application Layer Protocol: Web Protocols
Description: Adversaries may communicate using the application layer protocols associated with web traffic to avoid detection/network filtering by blending in with legitimate traffic. They often use port 443 (HTTPS).
Relevance: Since the connection is happening over port 443, the use of a common web protocol like HTTPS to conceal malicious traffic is a common technique.
T1090.002 - Proxy: External Proxy
Description: Adversaries may use external proxies to obfuscate their command and control communications by routing traffic through an external proxy such as a SOCKS proxy.
Relevance: The command includes :socks, indicating the use of a SOCKS proxy to relay traffic, which is common for masking communications between an infected host and the attacker’s infrastructure.
T1036.005 - Masquerading: Match Legitimate Name or Location
Description: Adversaries may use masquerading by placing an executable in a legitimate path, using a legitimate-sounding name, or leveraging built-in system executables (e.g., conhost.exe).
Relevance: The path C:\Users\Public\ combined with a legitimate-sounding executable like conhost.exe suggests potential masquerading.
Observations and Focus Areas
With these techniques in mind, here are some key indicators to investigate for this threat hunt:
Network connections initiated from binaries in C:\Users\Public\ or its subfolders. In my experience, very few legitimate executables should be making network connections from this location. Common false positives may include certain VPN clients or educational tools.
SOCKS client commands that are running throughout your environment.
Common Windows binaries executing from unusual directories.
Continuous Improvement: Close Visibility Gaps
For this threat hunt, we must confirm our visibility into these activities:
Do we have process creation/process tracking events that include command-line activity?
Are we monitoring network connection events, specifically those originating from our areas of concern?
While performing your threat hunt, you may find that you do not have the visibility, telemetry, or access required to answer important questions. That’s a great finding! Threat hunting will force you to identify and confront these types of gaps before an incident.
Continuous Improvement: Implement Better Detections
For detections, I highly recommend utilizing SigmaHQ—a fantastic resource for threat research and detection development. Each detection is mapped to the MITRE ATT&CK framework and comes with references for further exploration. Here are some relevant detections that could enhance our coverage against the threat from our example:
Useful tip: Tools like uncoder.io or sigconverter.io will allow you to input a Sigma rule and output a hunting query that works with various tools. Check them out!
Conclusion
Threat hunting is about more than just chasing down the latest exploit or investigating novel malware. It’s about focusing your efforts where they matter most—on threats that pose a legitimate risk to your environment. By understanding the Pyramid of Pain, prioritizing relevant threats, and approaching each hunt with a structured strategy, you can vastly improve the effectiveness of your threat hunting program.
As I mentioned earlier we won’t always detect new threats before they’ve been discovered. Using the above methodology, we may find Chisel, or we may find any number of tools used by threat actors that share similar TTPs (regardless of hash, filename, destination IP, etc). We've also improved our detection capabilities, so whether it's Chisel or an entirely new tool, if it shares the same TTPs, we have a strong chance of detecting it.
By being methodical and purposeful in your hunts, you'll not only improve your detection capabilities, but also increase the difficulty for adversaries to operate undetected in your environment.

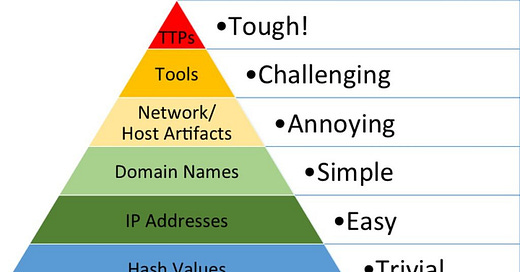


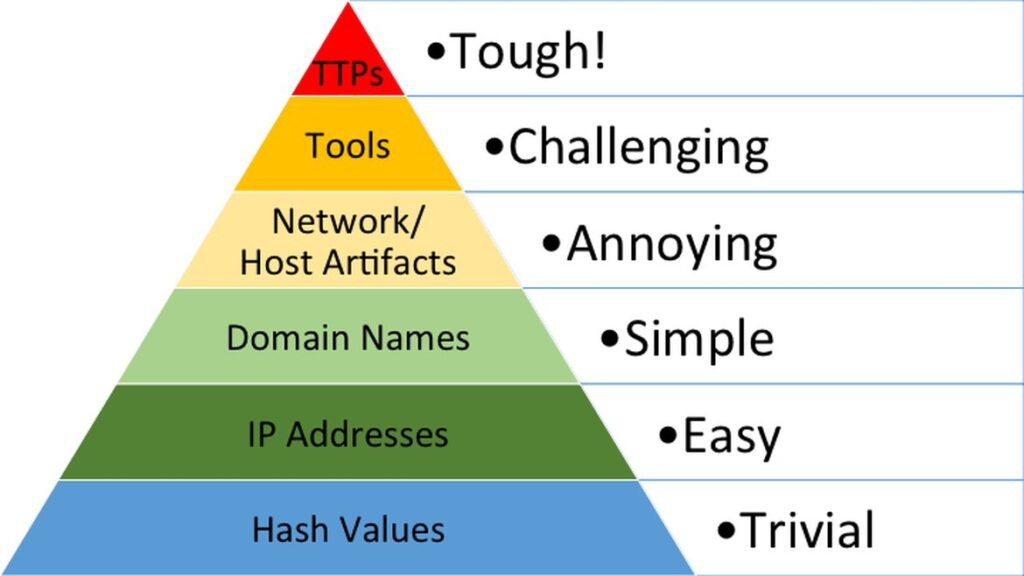

Bianco’s Pyramid of Pain